Aol Mail Old Sent Mail Sent Out Again
What is "AOL Email Scam"?
"AOL Email Scam" is another spam electronic mail campaign used past cyber criminals. Dissimilar most of these campaigns, which attempt to play a joke on users into downloading/installing malware or sending coin to cyber criminals, "AOL Email Scam" attempts to fox them into inbound AOL email account credentials.
This method is called phishing. Criminals transport thousands of deceptive email messages stating that users' accounts are about to be "shutdown" and encourage them to cancel the process. This is all simply a scam.
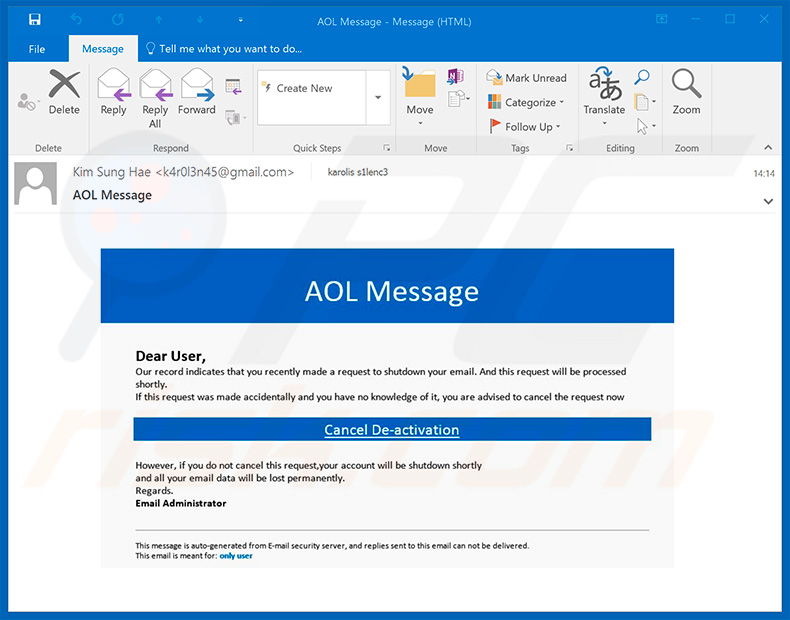
"AOL Email Scam" overview
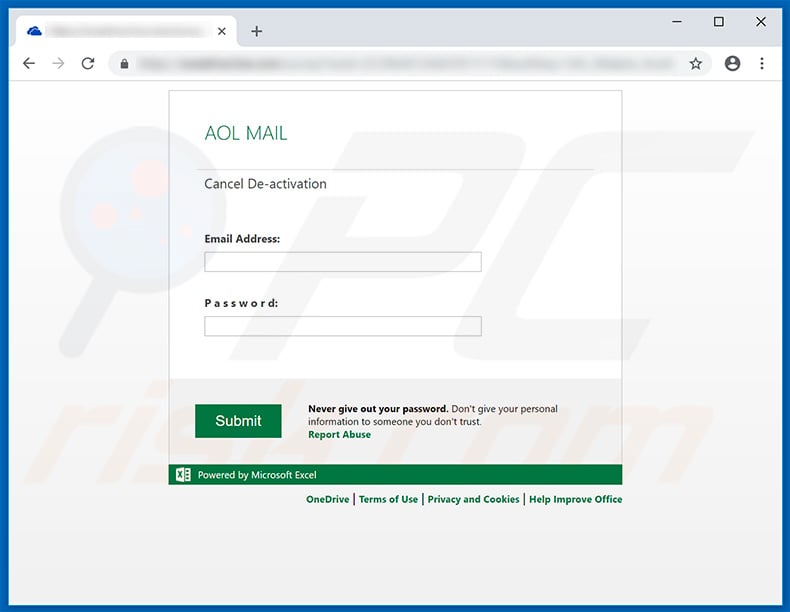
"AOL Email Scam" emails state that AOL Postal service administrators have recently received an business relationship-deletion request from the user. It is also stated that if this is a mistake and the account is not required to be deleted, the user must cancel the entire process by clicking the link provided. Be enlightened, however, that the link address leads to a fake AOL Mail website containing a login screen.
When users enter their login/password information, the details are immediately saved to a remote server and cyber criminals proceeds access to their accounts. Be aware that AOL Post is a legitimate service/visitor and has zero to practise with this spam entrada.
Cyber criminals just merits to be employees of this company and send thousands of deceptive emails hoping that some people volition fall for the scam and enter their account credentials.
Hijacked accounts tin can be misused in various means: criminals might attempt to borrow money from victims' contacts, hijack other accounts via the "restore password" office, send deceptive messages to other people, and so on.
Therefore, existence hijacked in this mode can atomic number 82 to privacy issues, financial loss, and fifty-fifty identity theft. For these reasons, you should ignore all "AOL Email Scam" emails.
| Name | AOL Email Scam |
| Threat Blazon | Phishing, Scam, Social Technology, Fraud |
| Symptoms | Unauthorized online purchases, inverse online account passwords, identity theft, illegal access of one's estimator. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) | To eliminate possible malware infections, scan your reckoner with legitimate antivirus software. Our security researchers recommend using Philharmonic Cleaner. |
Spam campaigns in general
There are hundreds of spam campaigns online. For example, Yоu May Not Know Mе E-mail Scam, Wе Arе Nоt Going To Steal A Lot Of Fourth dimension Electronic mail Scam, Y.E Design E-mail Virus, and Christmas Greetings Email Virus. Some are used to extort money from gullible users by threatening them. In almost cases, cyber criminals use the so-called "sextortion" method.
They claim that they accept hijacked the reckoner webcam and microphone, and recorded the victim "masturbating". They state that they will share the video with all of the victim's contacts unless a ransom (which typically fluctuates betwixt $500 and $grand, in Bitcoins or another cryptocurrency) is paid.
Unfortunately, many users are tricked into paying even though no such videos actually be. Other spam campaigns proliferate high-hazard viruses, such as Emotet, Adwind, Hancitor, FormBook, etc.
These contain malicious attachments designed to infect computers. Infiltrated viruses typically tape personal data (saved logins/passwords, browsing history, keystrokes, etc.) and open "backdoors". Viruses of this type pose a significant threat to your privacy and computer safety.
How do spam campaigns infect computers?
As mentioned, spam campaigns that distribute viruses comprise malicious attachments (due east.yard., PDF files, Microsoft Office documents, executables, archives, etc.), however, the attachment must be downloaded and opened before information technology can do any damage. Therefore, the user's manual intervention is required.
If the zipper is an MS Role document, it usually asks to enable macro commands that download and install malware. Executables must be opened manually. Note that lack of knowledge of these threats and devil-may-care behavior are the master reasons for these infections.
How to avoid installation of malware?
The fundamental to computer condom is circumspection. To prevent these infections, be very cautious when browsing the internet. Think twice before opening whatever e-mail attachment. Files/links that are irrelevant and those received from suspicious/unrecognizable email addresses should never exist opened. If you lot receive such messages, delete them immediately.
Furthermore, have a reputable anti-virus/anti-spyware suite installed and running. These tools can detect and eliminate malware earlier it performs whatsoever malicious actions and the presence of this software is essential when trying to protect the organisation from viruses.
If you lot have already opened malicious attachments, we recommend running a browse with Philharmonic Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "AOL Electronic mail Scam" electronic mail message:
AOL Message
Love User,
Our tape indicates that you recently fabricated a asking to shutdown your email. And this request volition be processed shortly.
If this request was made accidentally and you accept no knowledge of it, you are advised to abolish the asking nowAbolish De-activation
However, if you practice not cancel this asking,your business relationship will be shutdown shortly
and all your email data will be lost permanently.
Regards.
Electronic mail AdministratorThis bulletin is aut-generated from E-mail security server, and replies sent to this electronic mail can not be delivered.
This email meant for: but user
Screenshot of the imitation AOL website:
Instant automatic malware removal: Manual threat removal might exist a lengthy and complicated procedure that requires avant-garde computer skills. Combo Cleaner is a professional automated malware removal tool that is recommended to become rid of malware. Download it by clicking the push button beneath:
▼ DOWNLOAD Combo Cleaner Past downloading any software listed on this website you hold to our Privacy Policy and Terms of Use. To apply full-featured product, you accept to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated past Rcs Lt, the parent company of PCRisk.com read more than.
Quick carte:
- What is AOL spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you vicious for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals apply deceptive emails to trick Internet users into giving abroad their sensitive private information, for case, login information for various online services, email accounts, or online cyberbanking data.
Such attacks are called phishing. In a phishing assail, cybercriminals unremarkably send an email bulletin with some pop service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (incorrect aircraft address, expired password, etc.), and place a link which they hope their potential victims will click on.
Subsequently clicking the link presented in such electronic mail bulletin, victims are redirected to a simulated website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another pop attack vector is e-mail spam with malicious attachments that infect users' computers with malware. Malicious attachments normally carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' primary goal is to trick their potential victims into opening an infected e-mail attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or vox messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While information technology'due south a more than complicated method to steal personal data (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals tin get a much wider array of information and can collect information for a long flow of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this example, users receive an email claiming that a cybercriminal could admission the webcam of the potential victim and has a video recording of one's masturbation.
To go rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals attempt to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing e-mail:
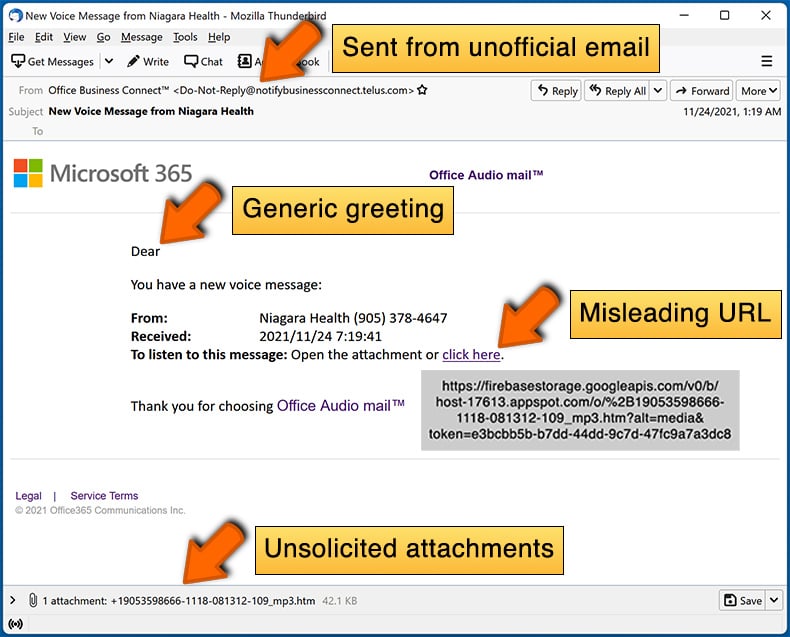
- Check the sender's ("from") email address: Hover your mouse over the "from" address and cheque if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Bank check for generic greetings: If the greeting in the e-mail is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most normally, companies phone call you lot by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the e-mail shows that it volition get to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's all-time not to click any links in the emails but to visit the company website that sent you the email in the outset identify.
- Don't blindly trust email attachments: Most commonly, legitimate companies volition ask yous to log in to their website and to view any documents there; if yous received an electronic mail with an attachment, it'due south a good idea to scan information technology with an antivirus application. Infected email attachments are a common assail vector used past cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you lot clicked on a link in a phishing email and entered your password - be certain to change your password every bit soon as possible. Usually, cybercriminals collect stolen credentials and and so sell them to other groups that utilise them for malicious purposes. If you change your password in a timely mode, there's a take chances that criminals won't have enough time to do whatever harm.
- If you entered your credit carte du jour information - contact your bank every bit shortly as possible and explain the state of affairs. There's a expert chance that you will demand to abolish your compromised credit carte and get a new one.
- If you see whatever signs of identity theft - you should immediately contact the Federal Trade Commission. This establishment will collect information nigh your situation and create a personal recovery plan.
- If you opened a malicious attachment - your calculator is probably infected, you lot should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI's Internet Crime Complaint Middle, National Fraud Data Middle and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
Spam emails are sent by the k; they are not personal.
I have provided my personal information when tricked by this spam email, what should I do?
If you've disclosed account log-in credentials - immediately modify the passwords of all potentially compromised accounts. And if you lot have provided other private data to the scammers (eastward.g., ID carte du jour details, credit card numbers, etc.) - contact the relevant government without delay.
I take read a spam e-mail only didn't open the attachment, is my computer infected?
No, reading a spam e-mail will not trigger any arrangement infection processes. Malware download/installation begins simply afterward the attachments or links present in these emails - are opened/clicked.
I have downloaded and opened a file attached to a spam email, is my computer infected?
Whether an infection was initiated might depend on the file's format. If it was an executable (.exe, .run, etc.) - most likely, yes - your system was infected. However, certificate formats (.doc, .exe, .pdf, etc.) may crave additional user interaction (e.g., enabling macro commands) to first downloading/installing malware.
Will Combo Cleaner remove malware infections present in electronic mail attachments?
Yes, Philharmonic Cleaner can discover and eliminate nigh all known malware infections. Information technology has to be stressed that performing a full system scan is essential - since sophisticated malicious programs usually hide deep within systems.
About the writer:

Tomas Meskauskas - adept security researcher, professional malware analyst.
I am passionate most figurer security and technology. I take an experience of over 10 years working in various companies related to computer technical effect solving and Internet security. I have been working equally an writer and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats. Contact Tomas Meskauskas.
PCrisk security portal is brought past a company RCS LT. Joined forces of security researchers help brainwash estimator users about the latest online security threats. More information nearly the visitor RCS LT.
Our malware removal guides are costless. However, if you want to back up us you tin can ship u.s.a. a donation.
gibbsprepition1988.blogspot.com
Source: https://www.pcrisk.com/removal-guides/14313-aol-email-scam
Post a Comment for "Aol Mail Old Sent Mail Sent Out Again"